Building a base of cybersecurity experts in Indiana - WISH-TV | Indianapolis News | Indiana Weather | Indiana Traffic

Inside the British military base where young hackers learn to stop cybercrime | UK security and counter-terrorism | The Guardian

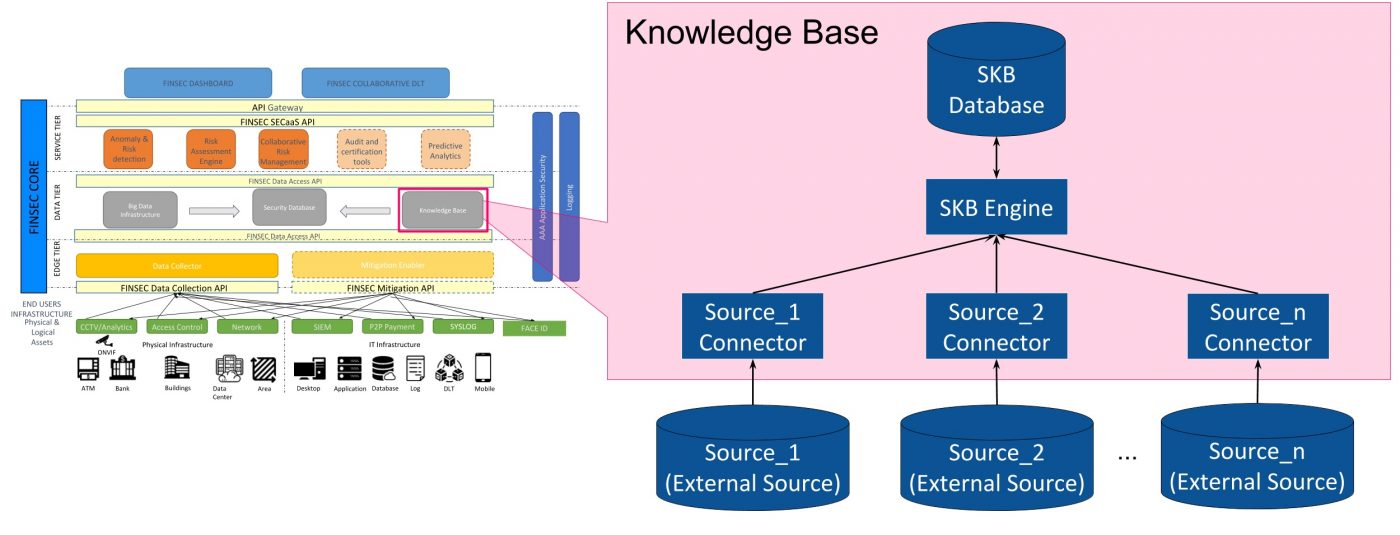
The architecture of the cybersecurity knowledge base. DDoS: distributed... | Download Scientific Diagram
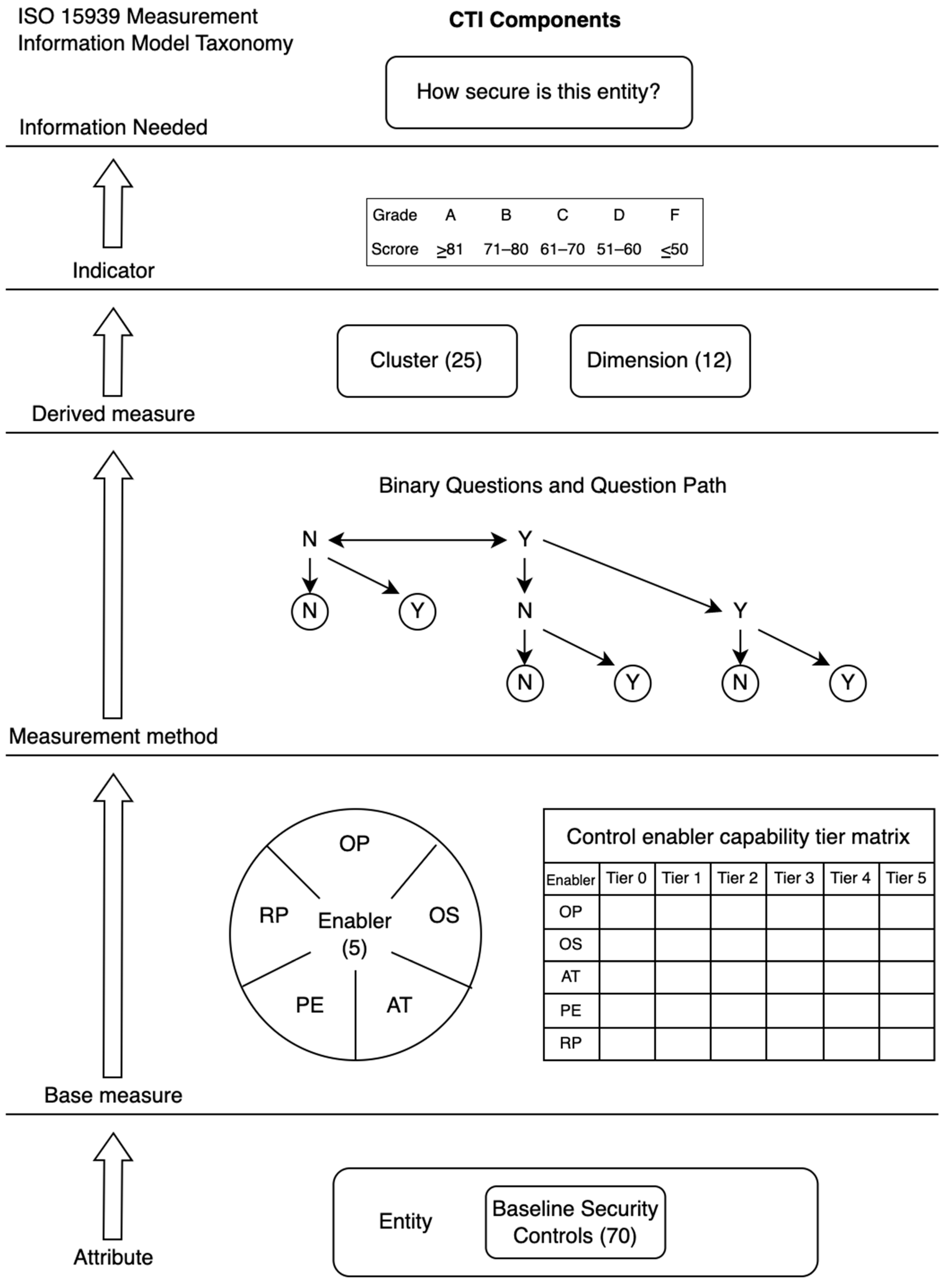
Applied Sciences | Free Full-Text | Cyber Trust Index: A Framework for Rating and Improving Cybersecurity Performance
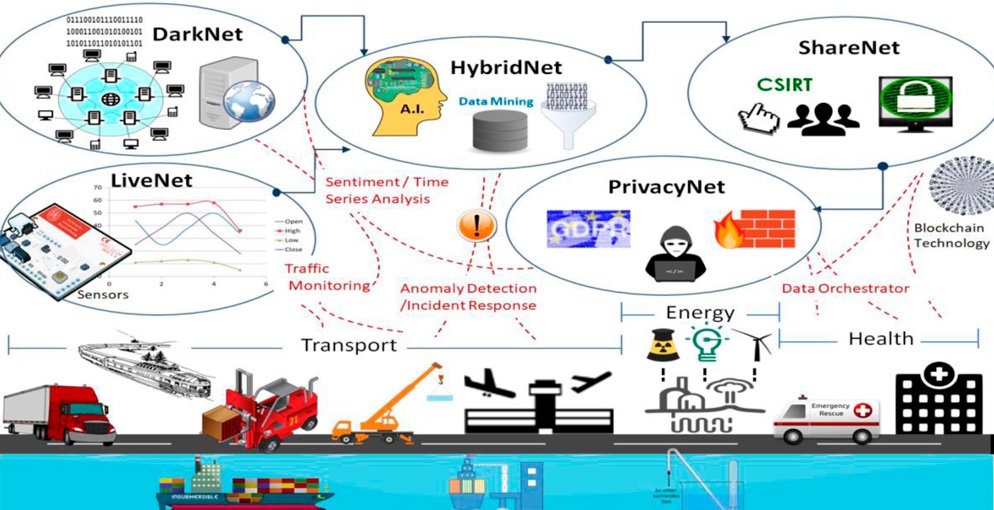
CYBERSANE - CYBER SECURITY INCIDENT HANDLING, WARNING AND RESPONSE SYSTEM FOR THE EUROPEAN CRITICAL INFRASTRUCTURES - Fundación Valenciaport