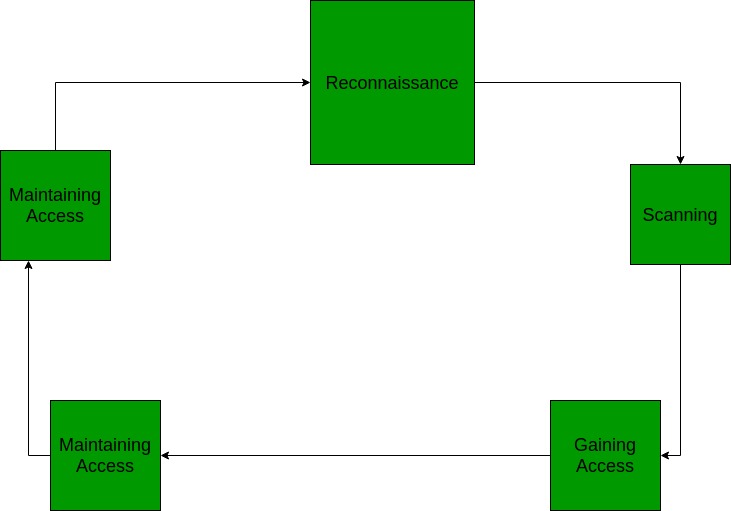
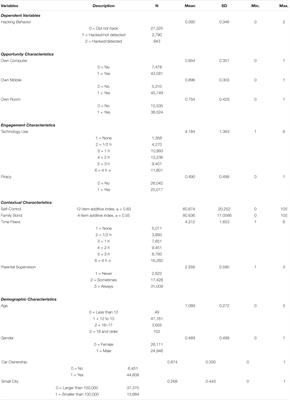
Despite Decades of Hacking Attacks, Companies Leave Vast Amounts of Sensitive Data Unprotected — ProPublica

All your Ether are belong to us (a.k.a Hacking Ethereum-based DApps) - Luis Quispe Gonzales - YouTube

Android for Hackers: How to Turn an Android Phone into a Hacking Device Without Root « Null Byte :: WonderHowTo